 OWASP Zed Attack Proxy 2.10.0
OWASP Zed Attack Proxy 2.10.0
A way to uninstall OWASP Zed Attack Proxy 2.10.0 from your PC
OWASP Zed Attack Proxy 2.10.0 is a Windows application. Read more about how to uninstall it from your computer. It was developed for Windows by OWASP ZAP. More information about OWASP ZAP can be seen here. Please open https://www.zaproxy.org/ if you want to read more on OWASP Zed Attack Proxy 2.10.0 on OWASP ZAP's web page. The program is often placed in the C:\Program Files\OWASP\Zed Attack Proxy directory. Keep in mind that this location can vary being determined by the user's choice. The complete uninstall command line for OWASP Zed Attack Proxy 2.10.0 is C:\Program Files\OWASP\Zed Attack Proxy\uninstall.exe. The application's main executable file has a size of 89.03 KB (91168 bytes) on disk and is named i4jdel.exe.The following executable files are incorporated in OWASP Zed Attack Proxy 2.10.0. They occupy 633.53 KB (648736 bytes) on disk.
- uninstall.exe (395.00 KB)
- ZAP.exe (149.50 KB)
- i4jdel.exe (89.03 KB)
This info is about OWASP Zed Attack Proxy 2.10.0 version 2.10.0 alone. Many files, folders and Windows registry entries can not be uninstalled when you remove OWASP Zed Attack Proxy 2.10.0 from your PC.
Folders left behind when you uninstall OWASP Zed Attack Proxy 2.10.0:
- C:\Program Files\OWASP\Zed Attack Proxy
Files remaining:
- C:\Program Files\OWASP\Zed Attack Proxy\db\db.properties
- C:\Program Files\OWASP\Zed Attack Proxy\db\hsqldb.properties
- C:\Program Files\OWASP\Zed Attack Proxy\db\mysql.properties
- C:\Program Files\OWASP\Zed Attack Proxy\db\mysql.schema
- C:\Program Files\OWASP\Zed Attack Proxy\db\zapdb.properties
- C:\Program Files\OWASP\Zed Attack Proxy\db\zapdb.script
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_ar_SA.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_az_AZ.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_bn_BD.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_bs_BA.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_ceb_PH.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_da_DK.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_de_DE.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_el_GR.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_es_ES.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_fa_IR.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_fil_PH.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_fr_FR.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_ha_HG.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_he_IL.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_hi_IN.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_hr_HR.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_hu_HU.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_id_ID.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_it_IT.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_ja_JP.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_ko_KR.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_mk_MK.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_ms_MY.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_nb_NO.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_nl_NL.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_pcm_NG.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_pl_PL.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_pt_BR.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_pt_PT.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_ro_RO.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_ru_RU.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_si_LK.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_sk_SK.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_sl_SI.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_sq_AL.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_sr_CS.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_sr_SP.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_tr_TR.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_uk_UA.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_ur_PK.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_vi_VN.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_yo_NG.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\Messages_zh_CN.properties
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_ar_SA.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_az_AZ.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_bn_BD.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_bs_BA.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_ceb_PH.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_da_DK.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_de_DE.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_el_GR.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_es_ES.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_fa_IR.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_fil_PH.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_fr_FR.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_ha_HG.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_he_IL.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_hi_IN.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_hr_HR.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_hu_HU.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_id_ID.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_it_IT.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_ja_JP.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_ko_KR.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_mk_MK.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_ms_MY.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_nb_NO.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_nl_NL.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_pcm_NG.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_pl_PL.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_pt_BR.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_pt_PT.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_ro_RO.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_ru_RU.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_si_LK.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_sk_SK.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_sl_SI.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_sq_AL.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_sr_CS.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_sr_SP.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_tr_TR.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_uk_UA.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_ur_PK.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_vi_VN.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_yo_NG.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lang\vulnerabilities_zh_CN.xml
- C:\Program Files\OWASP\Zed Attack Proxy\lib\bcmail-jdk15on-1.67.jar
- C:\Program Files\OWASP\Zed Attack Proxy\lib\bcpkix-jdk15on-1.67.jar
- C:\Program Files\OWASP\Zed Attack Proxy\lib\bcprov-jdk15on-1.67.jar
- C:\Program Files\OWASP\Zed Attack Proxy\lib\commons-beanutils-1.9.4.jar
- C:\Program Files\OWASP\Zed Attack Proxy\lib\commons-codec-1.15.jar
- C:\Program Files\OWASP\Zed Attack Proxy\lib\commons-collections-3.2.2.jar
You will find in the Windows Registry that the following keys will not be removed; remove them one by one using regedit.exe:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Uninstall\OWASP ZAP
A way to erase OWASP Zed Attack Proxy 2.10.0 with the help of Advanced Uninstaller PRO
OWASP Zed Attack Proxy 2.10.0 is an application released by OWASP ZAP. Sometimes, users choose to remove this application. Sometimes this can be difficult because doing this by hand requires some knowledge related to Windows program uninstallation. The best EASY solution to remove OWASP Zed Attack Proxy 2.10.0 is to use Advanced Uninstaller PRO. Take the following steps on how to do this:1. If you don't have Advanced Uninstaller PRO already installed on your Windows system, add it. This is a good step because Advanced Uninstaller PRO is a very efficient uninstaller and all around utility to take care of your Windows computer.
DOWNLOAD NOW
- go to Download Link
- download the program by pressing the green DOWNLOAD button
- set up Advanced Uninstaller PRO
3. Click on the General Tools category
4. Press the Uninstall Programs tool
5. All the applications existing on the PC will be shown to you
6. Navigate the list of applications until you find OWASP Zed Attack Proxy 2.10.0 or simply activate the Search field and type in "OWASP Zed Attack Proxy 2.10.0". If it exists on your system the OWASP Zed Attack Proxy 2.10.0 app will be found automatically. After you click OWASP Zed Attack Proxy 2.10.0 in the list of applications, some information regarding the program is made available to you:
- Safety rating (in the lower left corner). The star rating tells you the opinion other people have regarding OWASP Zed Attack Proxy 2.10.0, ranging from "Highly recommended" to "Very dangerous".
- Opinions by other people - Click on the Read reviews button.
- Technical information regarding the program you are about to remove, by pressing the Properties button.
- The publisher is: https://www.zaproxy.org/
- The uninstall string is: C:\Program Files\OWASP\Zed Attack Proxy\uninstall.exe
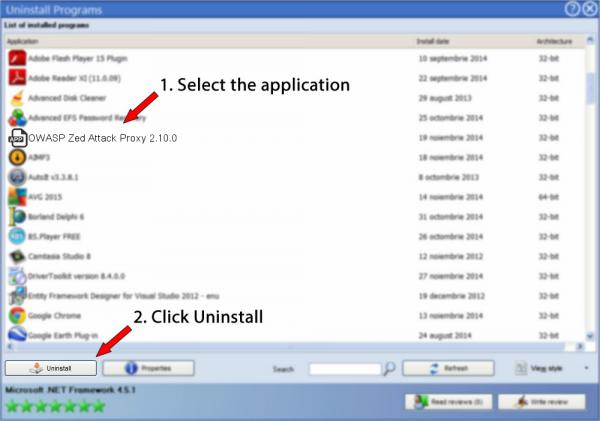
8. After removing OWASP Zed Attack Proxy 2.10.0, Advanced Uninstaller PRO will ask you to run a cleanup. Click Next to start the cleanup. All the items that belong OWASP Zed Attack Proxy 2.10.0 which have been left behind will be detected and you will be asked if you want to delete them. By uninstalling OWASP Zed Attack Proxy 2.10.0 using Advanced Uninstaller PRO, you are assured that no Windows registry entries, files or folders are left behind on your system.
Your Windows PC will remain clean, speedy and able to take on new tasks.
Disclaimer
The text above is not a piece of advice to uninstall OWASP Zed Attack Proxy 2.10.0 by OWASP ZAP from your PC, we are not saying that OWASP Zed Attack Proxy 2.10.0 by OWASP ZAP is not a good application for your PC. This text simply contains detailed instructions on how to uninstall OWASP Zed Attack Proxy 2.10.0 supposing you want to. The information above contains registry and disk entries that our application Advanced Uninstaller PRO discovered and classified as "leftovers" on other users' computers.
2020-12-26 / Written by Daniel Statescu for Advanced Uninstaller PRO
follow @DanielStatescuLast update on: 2020-12-26 20:37:36.560